-
- Downloads
add new Mastersthesis.pdf and Mastersthesis.blg files; update references.bib...
add new Mastersthesis.pdf and Mastersthesis.blg files; update references.bib with additional sources
Showing
- Thesis_Docs/Nikkhah_Nasab-Aida-Mastersthesis.blg 56 additions, 0 deletionsThesis_Docs/Nikkhah_Nasab-Aida-Mastersthesis.blg
- Thesis_Docs/Nikkhah_Nasab-Aida-Mastersthesis.pdf 0 additions, 0 deletionsThesis_Docs/Nikkhah_Nasab-Aida-Mastersthesis.pdf
- Thesis_Docs/main.tex 64 additions, 40 deletionsThesis_Docs/main.tex
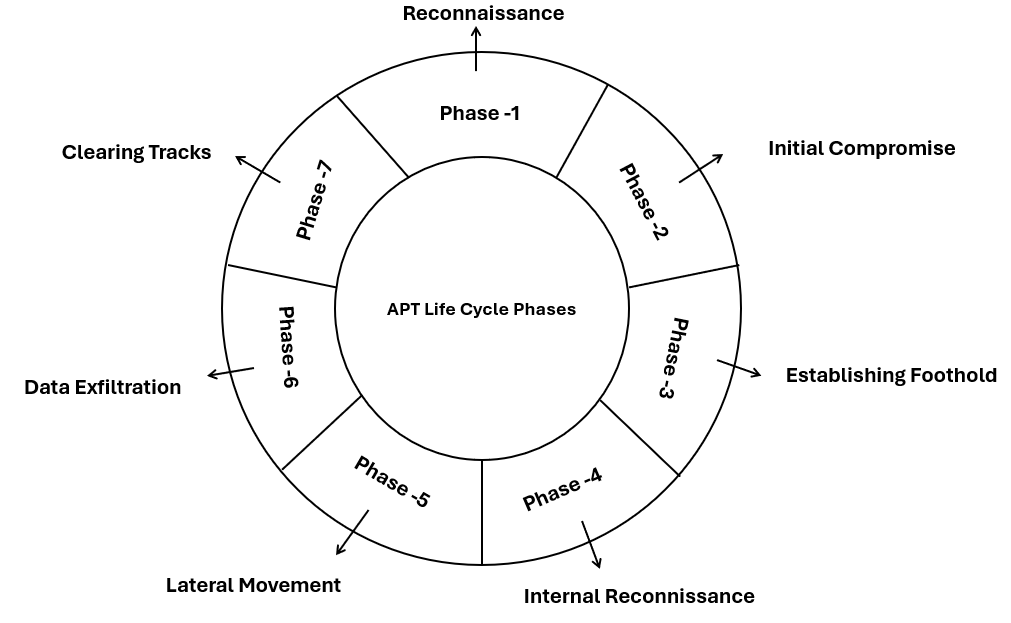
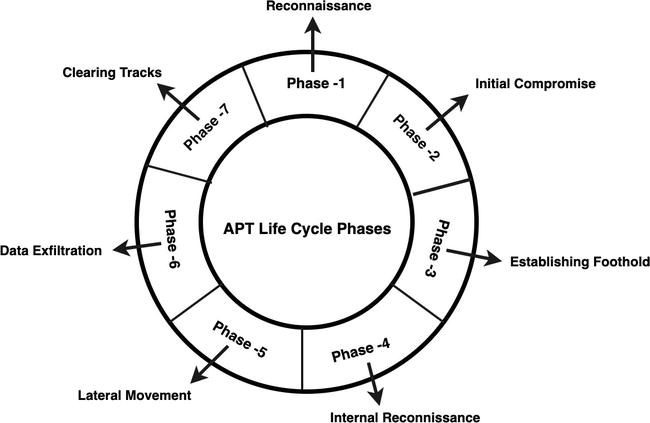
- Thesis_Docs/media/apt_attack_lifecycle.png 0 additions, 0 deletionsThesis_Docs/media/apt_attack_lifecycle.png
- Thesis_Docs/sources/references.bib 28 additions, 8 deletionsThesis_Docs/sources/references.bib
File added
| W: | H:
| W: | H: