-
- Downloads
update Mastersthesis.pdf and main.tex to refine content, improve clarity, and...
update Mastersthesis.pdf and main.tex to refine content, improve clarity, and remove outdated references
Showing
- Thesis_Docs/Nikkhah_Nasab-Aida-Mastersthesis.pdf 0 additions, 0 deletionsThesis_Docs/Nikkhah_Nasab-Aida-Mastersthesis.pdf
- Thesis_Docs/main.tex 12 additions, 14 deletionsThesis_Docs/main.tex
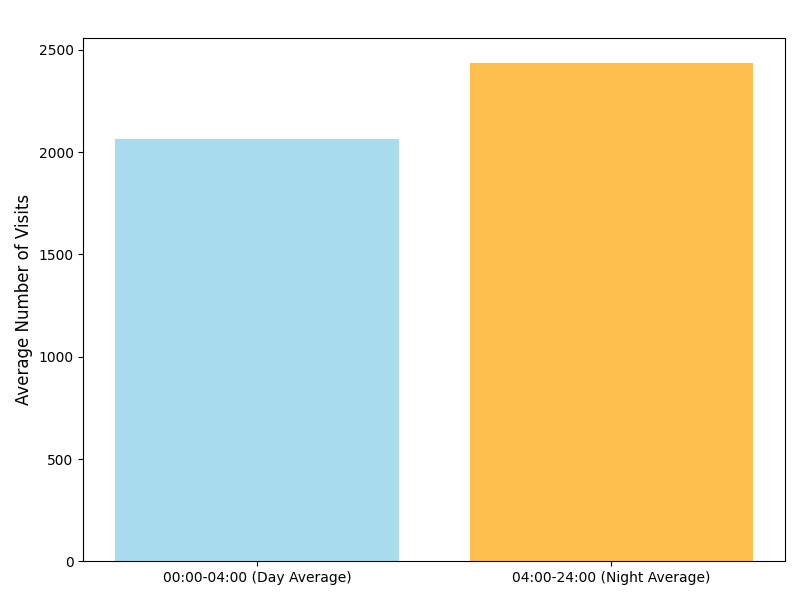
- Thesis_Docs/media/avg_day_night.png 0 additions, 0 deletionsThesis_Docs/media/avg_day_night.png
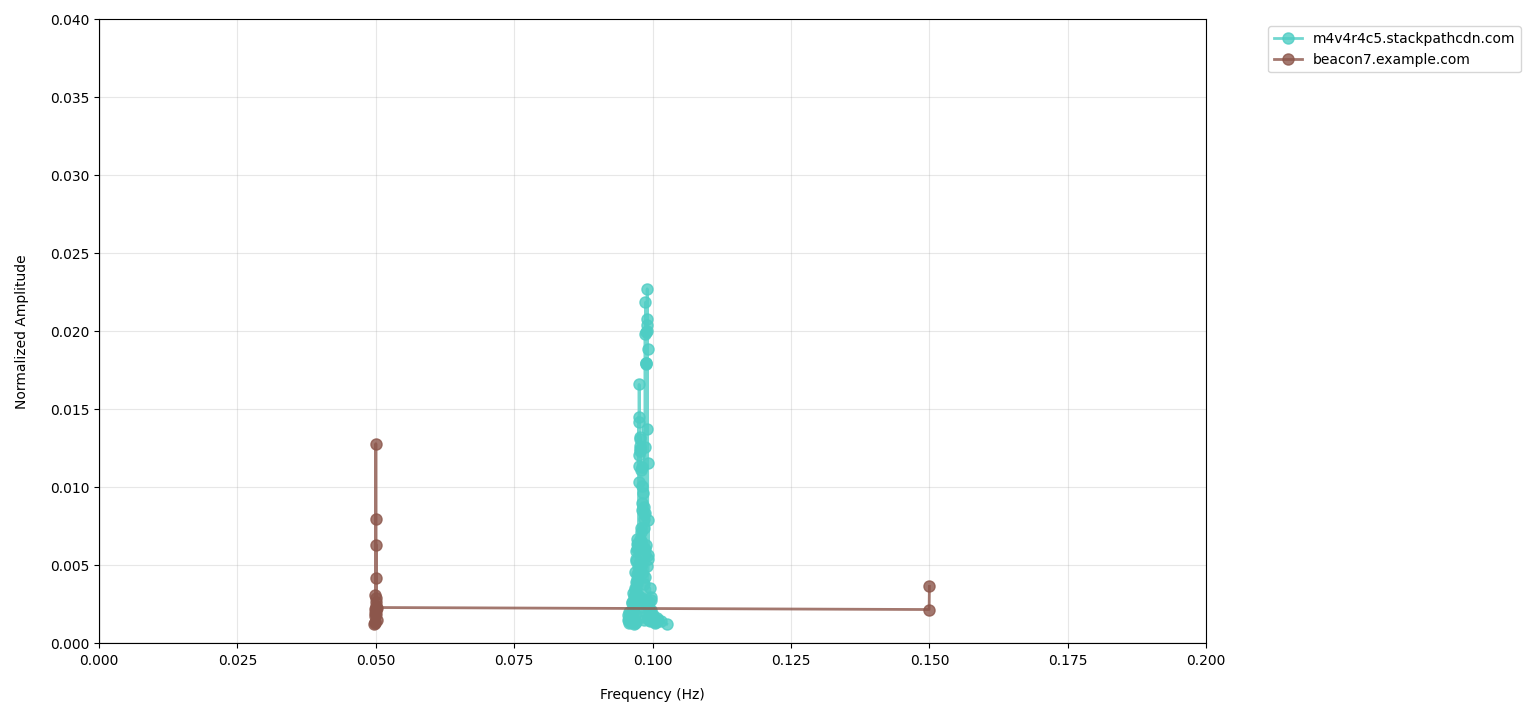
- Thesis_Docs/media/candidates.png 0 additions, 0 deletionsThesis_Docs/media/candidates.png
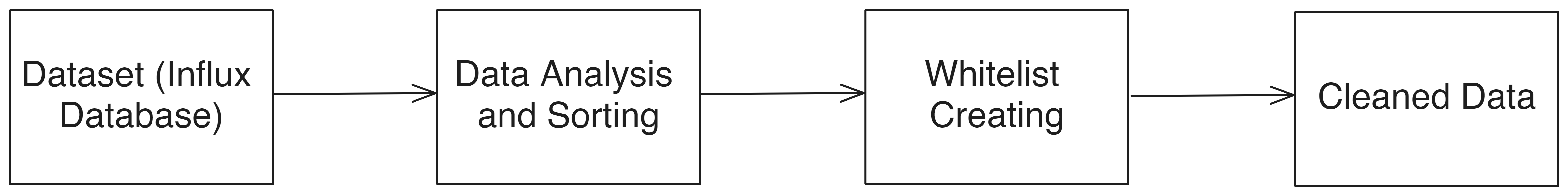
- Thesis_Docs/media/datasetchart.png 0 additions, 0 deletionsThesis_Docs/media/datasetchart.png
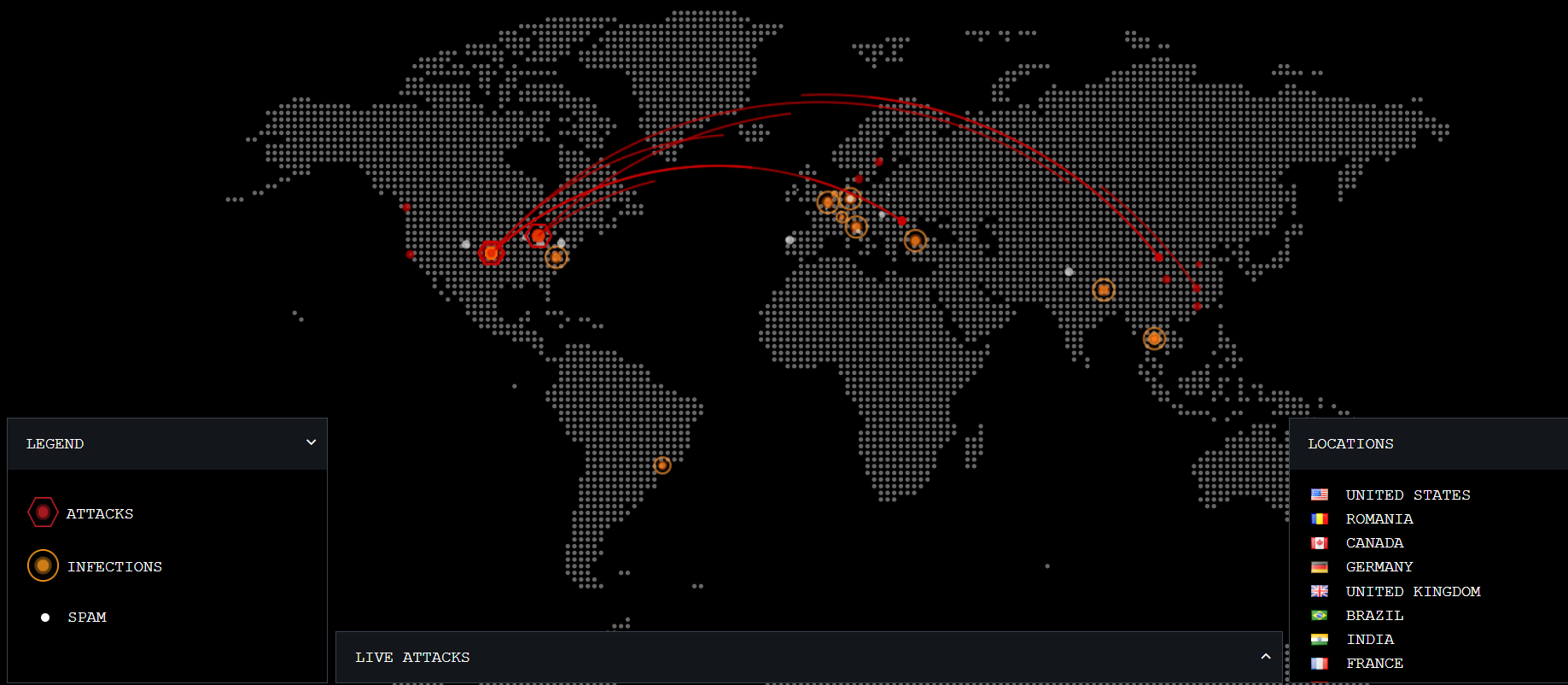
- Thesis_Docs/media/maps.png 0 additions, 0 deletionsThesis_Docs/media/maps.png
No preview for this file type
Thesis_Docs/media/avg_day_night.png
deleted
100644 → 0
18.5 KiB
| W: | H:
| W: | H:


Thesis_Docs/media/datasetchart.png
deleted
100644 → 0
170 KiB
Thesis_Docs/media/maps.png
deleted
100644 → 0
292 KiB